Email spoofing is currently one of the most significant phishing threats organisations face. It involves cybercriminals creating fake emails that appear to be from legitimate sources, such as Amazon, Microsoft, or DHL, to deceive employees into divulging sensitive information or performing harmful actions. The ability to distinguish between genuine and fraudulent emails can aid in safeguarding your organisation against expensive cyber security incidents.
1. Check the Sender's Domain and Email Address
Authentic organisations typically send emails from their official domain, such as "microsoft.com," and not variations like "microsoft.business.com." Phishing emails often use a fake or similar email address to appear legitimate. Therefore, it's important to scrutinise the sender's email address, particularly the domain name. If it appears suspicious, it's always best to delete the email without opening it.
2. Pay Attention to the Header and Footer
If the header or footer is inconsistent with other messages from that brand or has missing information, or appears hastily created, it's probable that the message is a phishing attempt.
Phishing emails often use fake or inconsistent branding to trick recipients into thinking they are receiving a legitimate email. Check the logo, font, and color scheme to ensure they match the company's branding. Also look out for low-quality images or images that don't load properly.
3. Look at the Subject Line and Preview Text
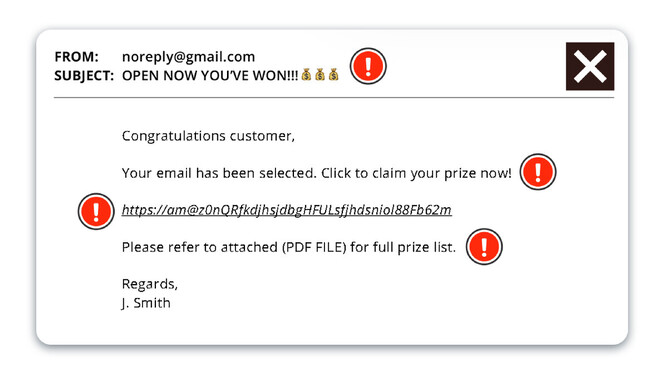
The subject line and preview text of an email are critical components that can help you determine whether an email is legitimate or a phishing attempt. Watch for threatening language, offers that seem too good to be true, missing or misleading subject lines, and overused capitalisation of letters. A lot of spam emails use multiple emojis to grab your attention, where many legitimate companies will limit their use of emojis.
4. Analyse the Content and Implied Urgency
Phishing emails often use urgent or threatening language to pressure the recipient into taking immediate action. Be wary of emails that create a sense of urgency or demand a response, such as "Your account has been compromised! Take action now!"
5. Be Wary of Unexpected Attachments
If you aren’t expecting an attachment or an attachment looks suspicious because it has a strange name, it might be malware or ransomware, which are frequently deployed through phishing.
Malware is often hidden in attachments with file types like .exe, .bat, or .js. Also be on the lookout for unusual, generic file names or password-protected files (as these can prevent your anti-virus software from scanning them).
6. Use Caution with Links
Consider the links that a message asks you to click, to see if they go to the company’s actual domain or log in on their site directly. Fraudulent password reset requests are a staple of phishing. Phishing emails often contain links or attachments that can infect your device with malware or direct you to a fake website designed to steal your login credentials. It's best to avoid clicking on any links or downloading attachments unless you are sure of the sender's legitimacy.
Better Safe Than Sorry
Regular security awareness training can empower employees to identify and prevent phishing attacks, which are among the most common methods cybercriminals use to infiltrate organisations. The good news is that by providing effective training, you can reduce the risk of your company falling victim to damaging cyberattacks, such as fake branded emails.
Our team can implement a security awareness training program to not only educate, but test your employees in controlled simulations. Over 90% of malware is delivered via email every day to inboxes worldwide. Be sure your team follow the correct procedures to keep your business safe!